Session Hijacking with firesheep
Hi guys , today in this tutorial we will tell you how to do session hijacking. This tutorial is very simple today, and it needs a little bit brain :D
Note- Please if you dont want to be in trouble use any vpn while doing this. Usuaally in internet cafes or your own private wifi , you dont have to worry :)
download free vpn- HERE
What is Session Hijacking
Every time you connected to the web application (usually a dynamic web application) you will have a unique ID called “session“, this session will identifies you as a valid user and will always valid until you kill the session (log out process) or the session has expired. Some bad people trying to identifies or guessing the session ID value to gain privileges as a valid user in a web application.
Firesheep HTTP Session Hijacking
Firesheep is a firefox (browser) extension add-on , to do the session hijacking. And the most interesting thing is that this tools can hijack Facebook, Twitter, WordPress, Amazon, etc from the valid user. The most important thing that this tools is very easy to configure and to launch an attack.
Follow steps-
2. Sit on a unencrypted wireless network or in simple word use internet on an internet cafe or a open wifi network
3. Turn on your wireless card(support promiscious mode, such as : atheros, orinocco, etc) and join the network
4. Start capturing with firesheep
5. Just wait until some user authenticate at the facebook, twitter, etc.
Step by Step Firesheep Configuration
1. The picture below is the interface of firesheep(click view –> sidebar –> firesheep) and you can click the red circle for preferences
2. In this picture you should choose which interface you want to capture the data. for example when you’re in a wireless network, you should activate the wireless adapter.
3. This picture below tells you which website session can hijacked handle by this addons.
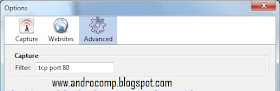
4. Usually when capturing data, will use TCP port 80, because if it’s 443 I think will be encrypted, but I still didn’t try for another port .
5. When you finish, click the “Start Capturing” and wait until someone authenticate some website on the website list.
by- ANS -VENTURE.






No comments:
Post a Comment